The next generation security tools are designed to help users keep pace with modern bad guys (skilled and motivated programmers, often with large resources) while simultaneously improving privacy, security, and system integrity. These tools are powered by intelligence, insights, signals, alerts from many systems, and continuous human testing, and can integrate with trusted partner systems as well.
MDATP
Microsoft Defender Advanced Threat Protection (MDATP) is one of the solutions in the Microsoft Security cross-cloud protection platform. It is built with a Security by Design approach. Various measures, signals, alerts, continuous testings, safeguards and best programming practices make sure of securing the foundation of Microsoft Defender Advanced Threat Protection. Today these systems are known as Artificial Intelligence (AI) and Machine Learning (ML) platforms.
A few of the most common attack techniques, tools, and procedures which MDATP can detect:
- Lateral Movement
- Pass the Ticket
- Valid Accounts
- Credential Dumping
- Kerberoasting
- Privilege Escalation
- Mimikatz
- PsExec
Alerts in the MDATP solution are aligned with the MITRE ATT&CK Matrix.
Detect Various Types of Attack Techniques in Near Real Time
Microsoft Defender ATP provides a comprehensive, well-organized portal to bring together all Alerting, Detection and Protection capabilities.
Microsoft Security Center Portal:
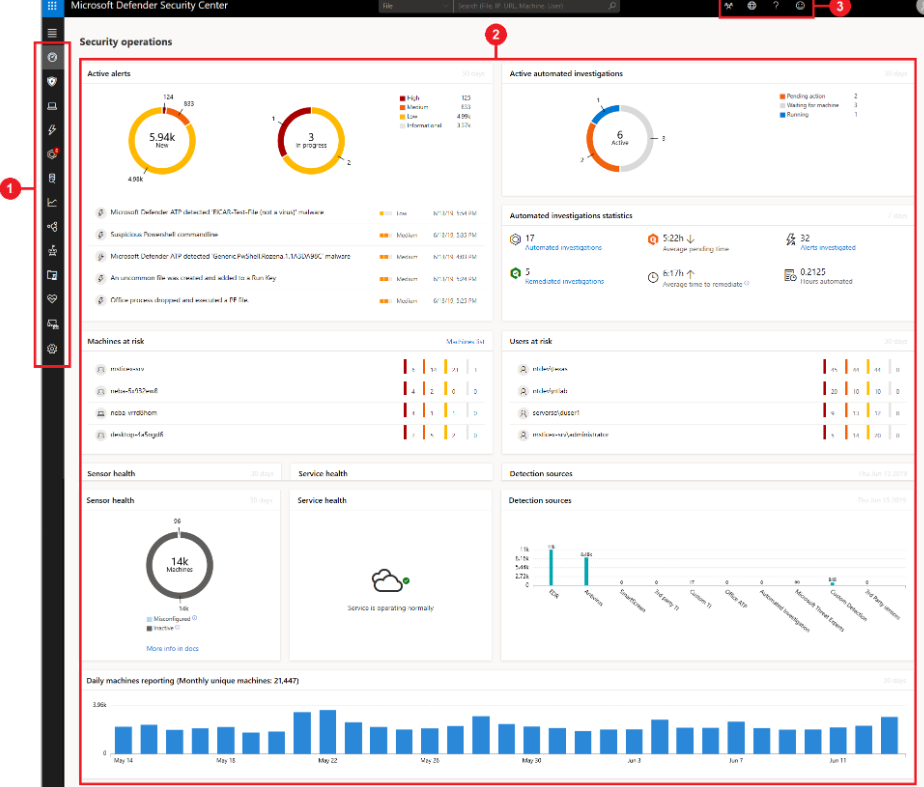
- The Security Center portal provides three main areas:
- (1) Navigation pane
- (2) Main portal
- (3) Search, Community center, Time settings, Help and support, Feedback
When a threat is detected by MDATP, alerts are created in the security center portal. The analyst can view them and correlate various tools, techniques, files, commands, and attack vectors. Security center stores alerts for six months, enabling an analyst to travel back in time to the start of an attack.
Start With Alerts and Incidents
The Alerts and Incidents view is the starting point for working with Microsoft Security Center. It shows all alerts and any active incidents from machines on your network. It can help define priorities for investigation and separate false positives from real threats.
When a threat has been detected, there is an option to select the detailed view and filter alert data based on severity, category, technique, and much more. Selecting a certain alert gives you an option to see all details and information about the alert.
In the Microsoft Security Center Portal, the Navigation Pane area gives you access to the Alert Investigation Pane for each alert with all necesary details such as:
- Severity
- Category
- Detection Source (1)
- Alert Context
- Status
- Description
- Recommended Actions
- Alert Process Tree (2)
Note:
- (1) Detection source is integrated with other Microsoft Security Products.
- (2) The Alert Process Tree provides deep triage for investigation displaying the aggregated alert and surrounding evidence that occurred within the same execution context and time period.
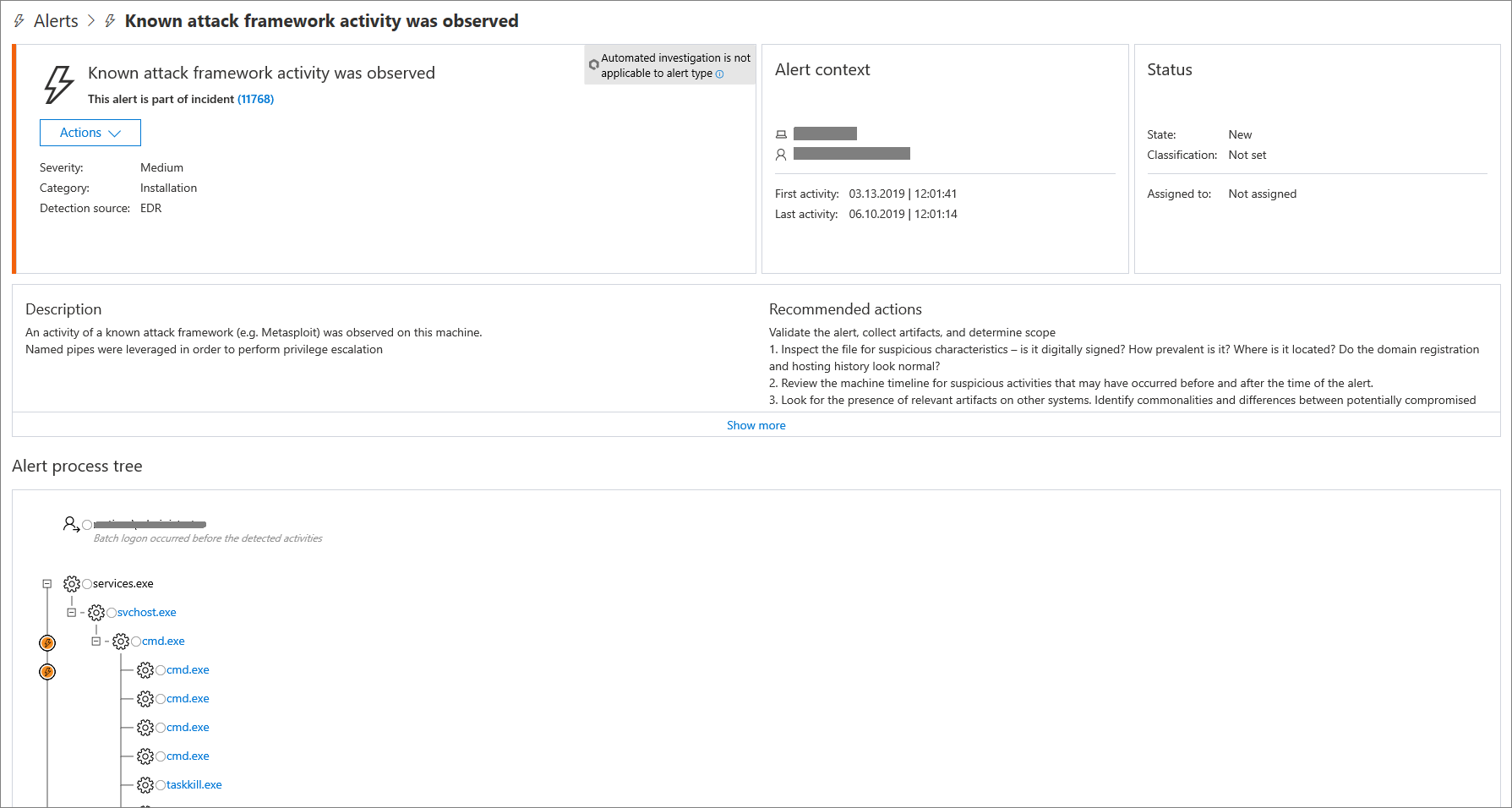
The Alert Process Tree provides a rich detailed view of the investigation context:
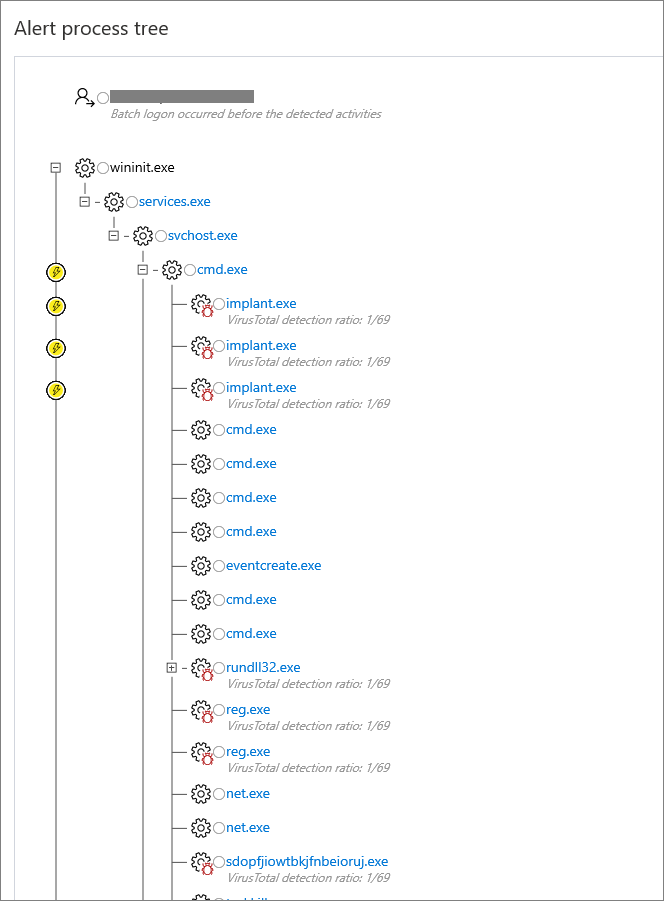
Note:
- The alert process tree might not show for some types of alerts, particulary those that were not triggered directly by process activity.
- Clicking in the circle left to the indicator displays details.
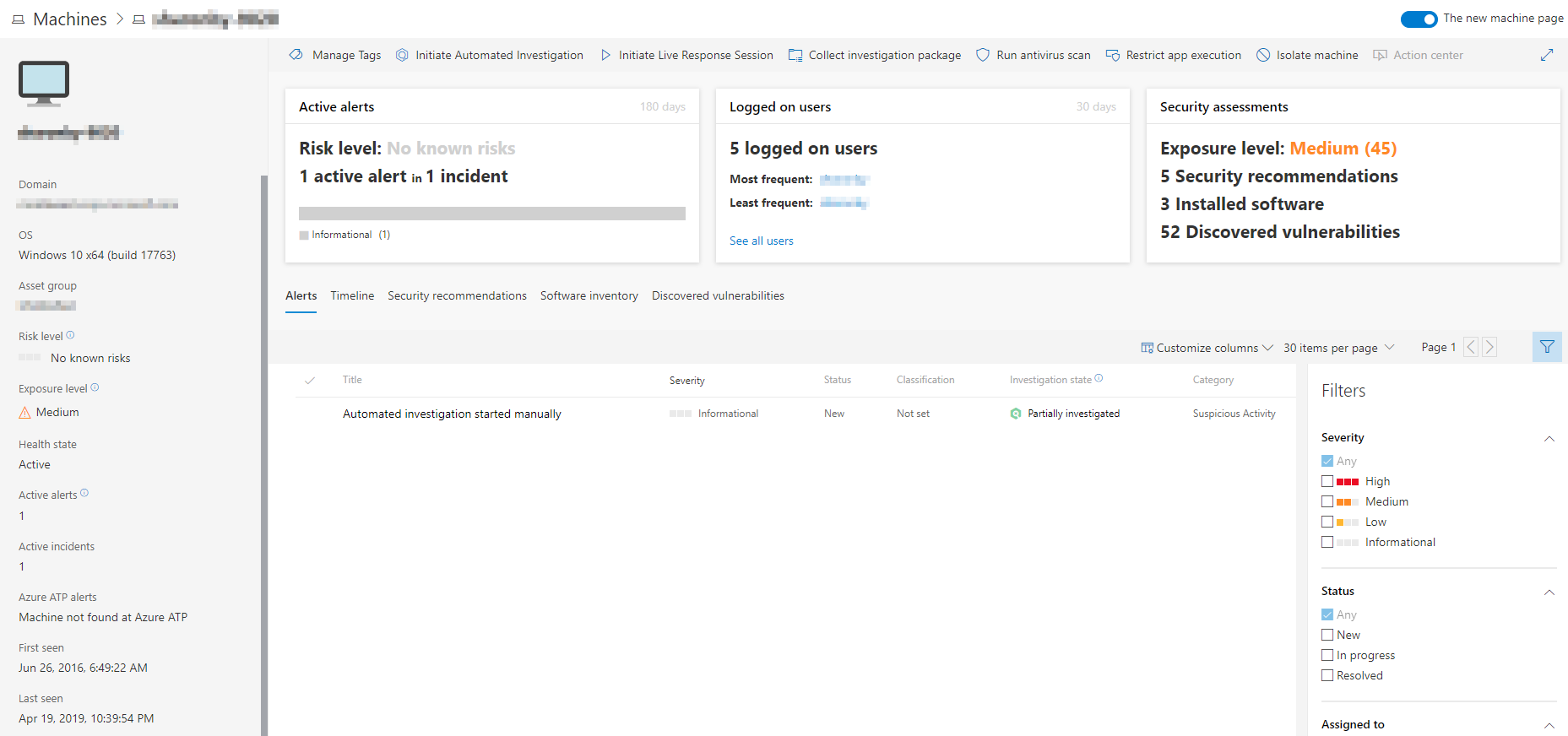
Investigating Machines
It is possible to investigate several machines with related detected alerts in order to identify suspicious behaviour or a potential breach. Each affected machine has a timeline report with many areas and details.
When investigating a specific machine, there are options to see different details such as:
- Machine details
- Response actions
- Cards (active alerts, logged on users, security assessment)
- Tabs (alerts, timeline, security recommendations, software inventory, discovered vulnerabilities)
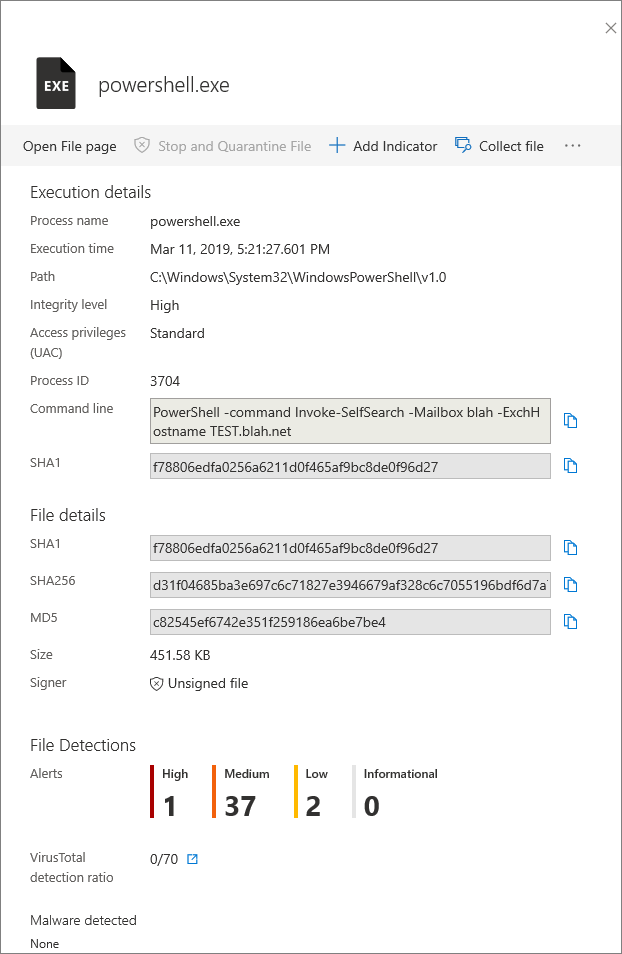
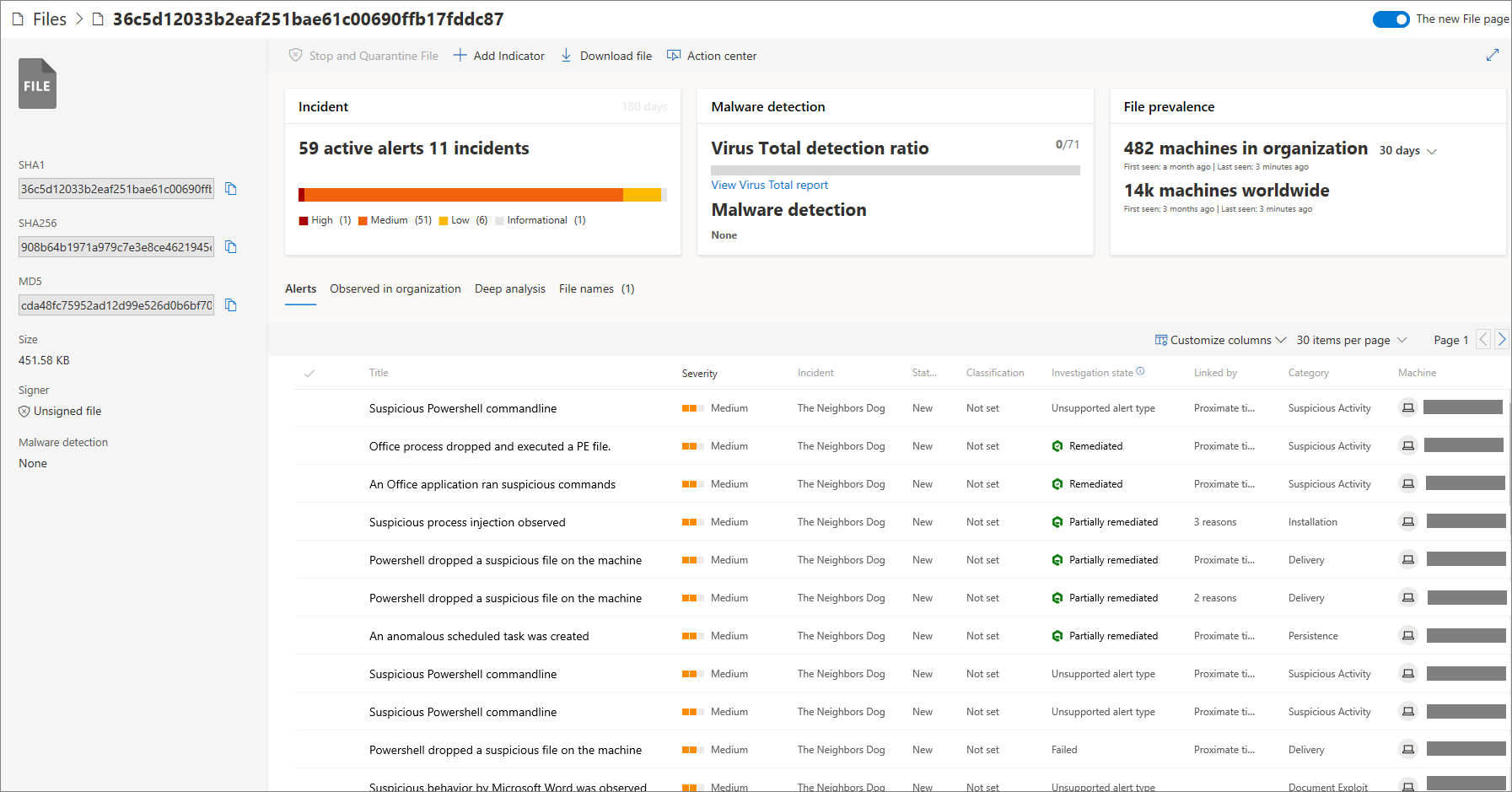
Investigating Files
Each detected alert (suspicious behaviour or event), may have files associated with it. These files can identify malicious activity or the potential scope of the breach. The file section of the alert view has an option to filter different views and options to trigger remediation actions. It will also display various attributes about the file to help understand what it is.
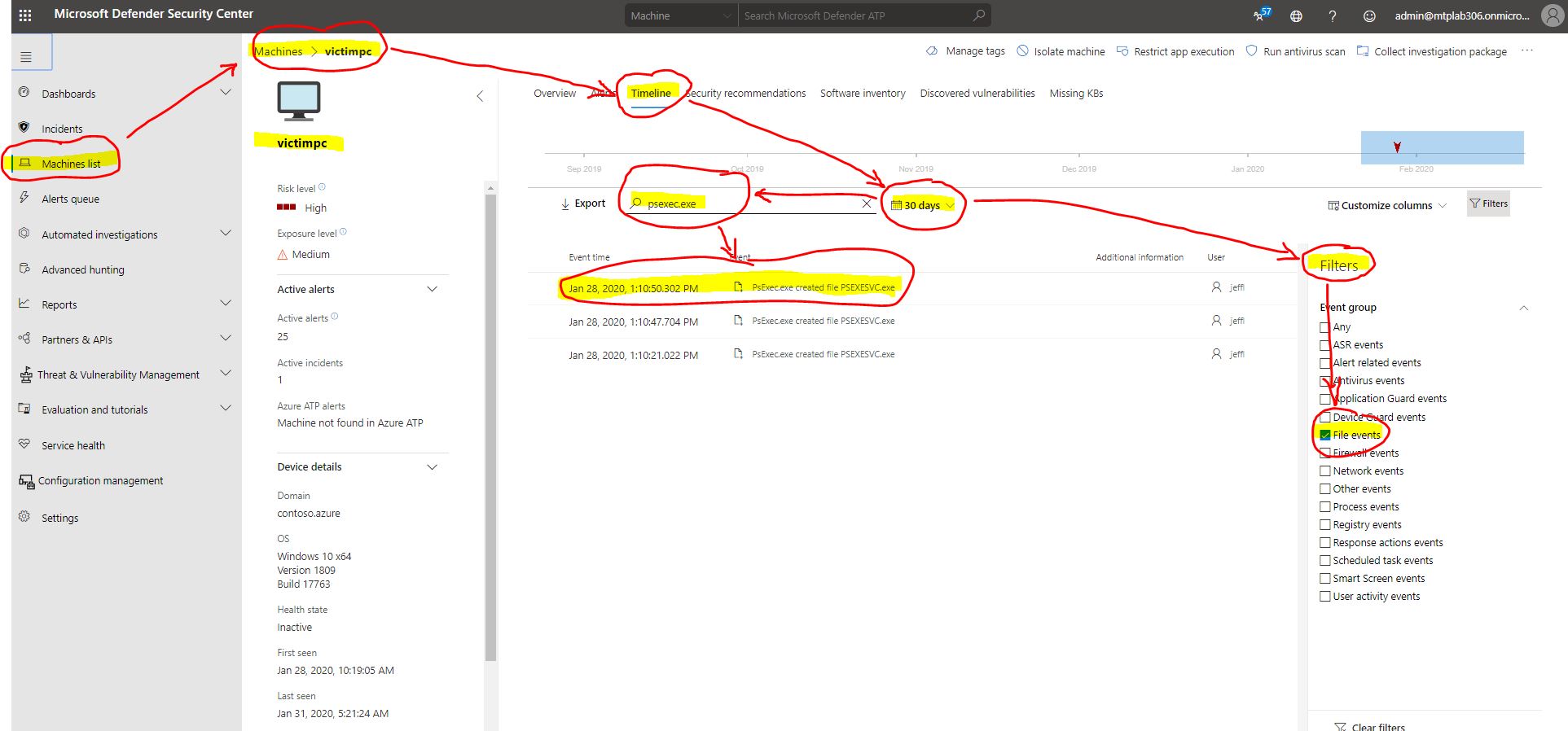
Sometimes you might wonder about the time when a certain malicious activity started. Detected alerts or malicious files created in the past could be related to the timeline and suspicious behaviours happening at this very moment. Correlation of suspicious events are crucial in these situations. Something which happened 30 days ago could be the starting point for spreading malicious activities across the network much later.
A great feature to make your life easier is the Filters Event Group with the option to search back in time for suspicious processes or commands used to create malicious files. All can be found on the affected machine page by selecting timeline, choosing a custom date in the past, using the desired filter group and finally using the search box to look for a malicious process.
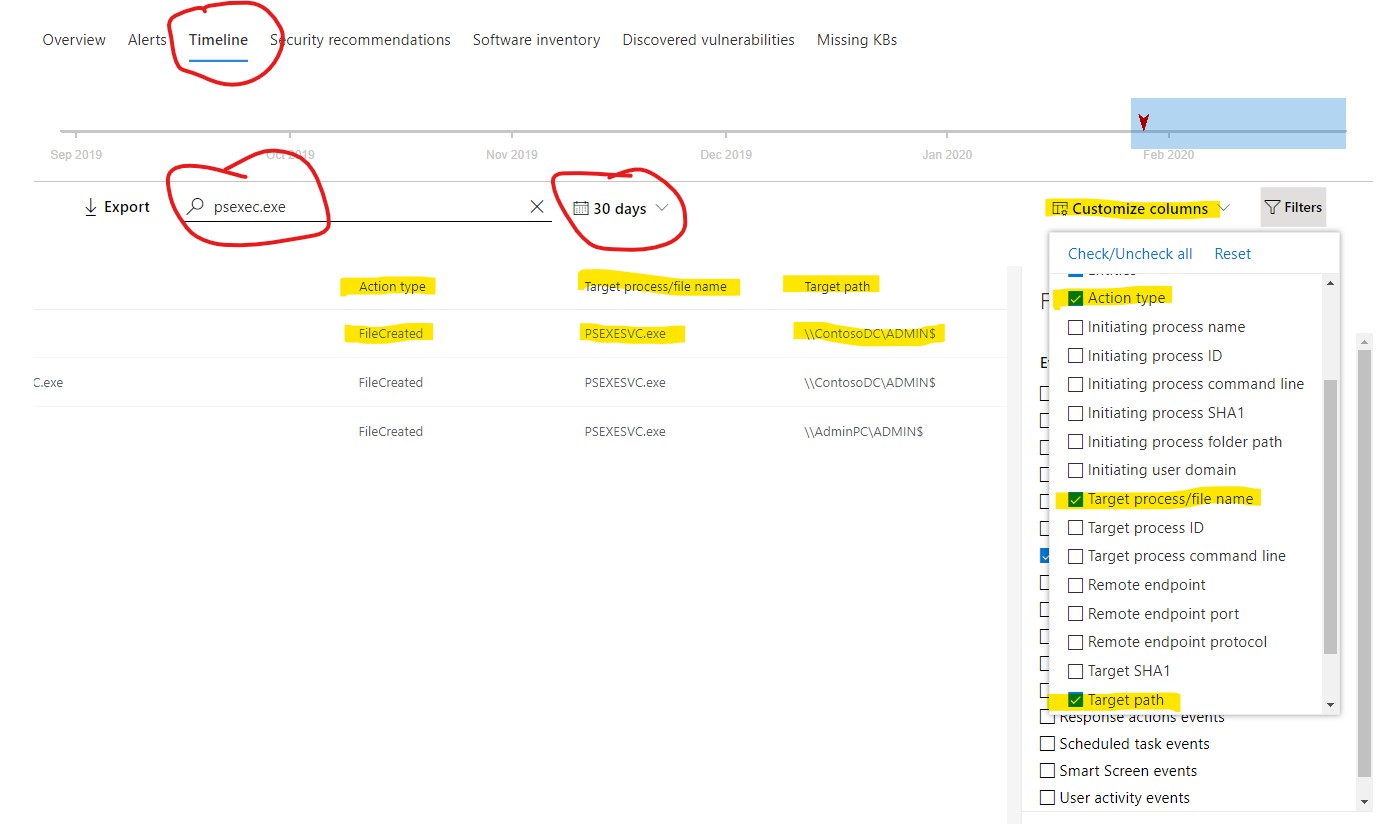
Better yet, there is one more handy feature you can use so that you wouldn’t have to search through all of the events, looking for the exact name of the malicious file created and location (path). This option can easily help you customize the columns view in the central overview pane. Do this by choosing the desired filter/parameters from the drop down menu from the Customize columns option on the right side of the screen.
Conclusion
We see a lot of platforms today built on similar concepts. But as mentioned before, technology, no matter how good, without the human factor will not have the desired outcome for your Cloud Cyber Security journey. Microsoft Defender ATP can be a boarding pass into the exciting new world of Cloud Cyber Security. Make no mistake, a long journey awaits you, but tools like this will help combine solid security with good workflows for security analysts. Microsoft Defender ATP can provide a great foundation in overall security strategy, and also lower the security risk. Remember, Microsoft Defender ATP is just a piece in the puzzle, which you have to put together.
To find more detailed information about this tool, please visit Microsoft Defender ATP, and if you want to know what others think about it, visit MITRE evaluation highlights.

